What are they?
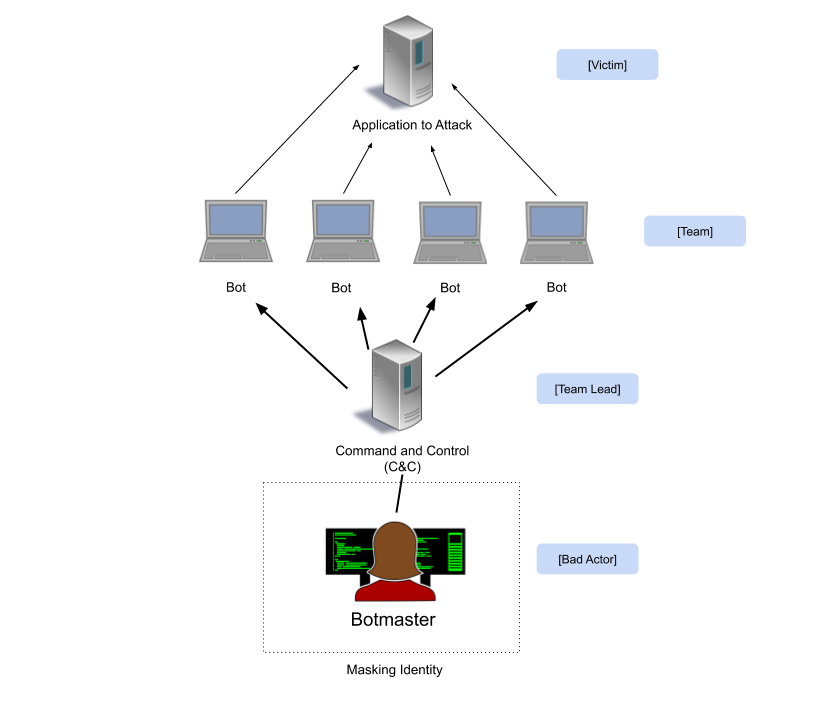
Botnets are a team composed of computers. Each team member, computer, work together to accomplish a goal. The team of computers are known as bots.
Most teams have a leader, this is known as the botnet’s command and control (C&C) – that is to say, where the bots receive commands from.
A botnet is typically formed by compromising multiple machines. When a machine is compromised, bad actors have access to your personal information and can utilize your machine’s resources to accomplish tasks. The bad actor can either take complete control over the machine or use some resources stealthily, without the user knowing, to perform attacks on other systems.
How do devices become bots?
Machines can be compromised and used as a bot when infected by malware. Actions like clicking on a phishing email, downloading a malicious PDF, going on a malicious website, downloading malicious software, and more, can compromise a machine.
Also, devices can be compromised if it has a default password set because those passwords are much simpler to crack. Such devices with default credentials have a high chance of being a part of a botnet. Thus, it is best to always change the default password on a device to a unique password.
Apart from compromising devices, botnets can also be purchased or rented with minimal effort.
What are they used for?
Botnets are known for DDoS attacks as well as mining cryptocurrencies.
Prevent your machine from becoming a bot
- Be cautious when clicking on links. You can use tools like VirusTotal to check links before clicking on them.
- Always keep all your applications up to date. Updates fix bugs and some vulnerabilities that were identified.
- Keep an eye out for phishing emails. Some may seem they come from someone you know and ends up being a bad actor wanting to download malicious files or make you click on a link. To analyze emails, review the header.
- Scan downloaded files. Most malicious files require execution, so before opening, use a scanner like VirusTotal.
- Use antivirus software. Something is better than nothing.